Collaboration is critical to take down today’s most advanced adversaries. CrowdStrike regularly works with law enforcement agencies and industry leaders to identify, track and stop cyber threats. We recently cooperated with the Department of Justice as part of a broader effort to disrupt two individuals heavily involved in operating Anonymous Sudan. In this blog, we discuss the hacktivist group’s history, targeting patterns, motivations and threat activity, which ultimately led to today’s indictment.
Anonymous Sudan, a group known for their large-scale distributed denial-of-service (DDoS) attacks, emerged in January 2023. They quickly gained notoriety for claiming responsibility for a string of high-profile attacks. The group’s activities — as detailed below — were unusual in nature, combining politically motivated targeting with attacks on large tech companies, more likely oriented around seeking attention. This strange mix of motives, coupled with their religious stance and alliances with Russian hacktivist groups, fueled speculation about their true origins and goals.
Today, the U.S. Department of Justice unsealed the indictment against two Sudanese men accused of orchestrating the Anonymous Sudan hacktivist group. This announcement provides strong evidence against previous theories that the group was a front for government-backed attacks. The two men mentioned in the indictment are the brothers Ahmed Salah Yousif Omer and Alaa Salah Yusuuf Omer. While the older brother, Alaa Salah, developed the tool chain running on the attack infrastructure, the younger brother, Ahmed Salah, is charged with tasking the attacks and with maintaining the group’s online presence by operating various social media channels.
Between January 2023 and March 2024, Anonymous Sudan conducted numerous DDoS attacks against various entities worldwide. After initially joining a brief pro-Russian hacktivist campaign, Anonymous Sudan conducted a series of DDoS attacks with apparent religious and Sudanese nationalist motivations, including campaigns against Australian and Northern European entities. The group was also a prominent participant in the annual #OpIsrael hacktivist campaign. Throughout these campaigns, Anonymous Sudan also demonstrated a willingness to collaborate with other hacktivist groups like Killnet, SiegedSec and Türk Hack Team. Notably, the group’s observed inactivity since March 2024 aligns with the timing of law enforcement actions against its members.
Anonymous Sudan consistently utilized social media platforms, notably Telegram, to claim responsibility for their attacks. They typically posted messages in Arabic, English and Russian, often detailing targeted entities and providing “check-status” links to verify website disruptions. Additionally, they leveraged visual elements like images and videos, sometimes incorporating pro-Russia or religious symbolism. The group also interacted with their followers on Telegram, responding to comments and sharing news articles about their activities. This strategic use of social media allowed them to publicize their operations, gain notoriety and potentially recruit other hacktivist groups for collaboration.
It is remarkable that just two individuals, with a relatively small investment of time and resources, were able to create and maintain a DDoS capability potent enough to disrupt major online services and websites. Their success stemmed from a combination of factors: a custom-built attack infrastructure hosted on rented servers with high bandwidth, sophisticated techniques for bypassing DDoS mitigation services, and the ability to quickly identify and exploit vulnerable API endpoints that, when overwhelmed with requests, would render services inoperable and disrupt user access.
Anonymous Sudan’s Targeting Patterns and Motivations
Outside of its high-profile technology sector targets, Anonymous Sudan frequently targeted entities in the telecommunications, healthcare, academic, aviation, government, media and financial sectors — often including critical infrastructure such as hospitals, airports, banks and telecommunications providers. The group’s geographic targeting scope was broad but most frequently involved targeting entities in Israel, the United Arab Emirates, India, the United States, Australia, Europe (including Sweden, Denmark, France and the United Kingdom), and Sudan’s near abroad (including Kenya, Nigeria, Egypt, Chad, Uganda and Djibouti).
This broad array of targeting reflects some of Anonymous Sudan‘s disparate motivations for their operations, which include acting on anti-Israeli, religious and Sudanese nationalist sentiments.
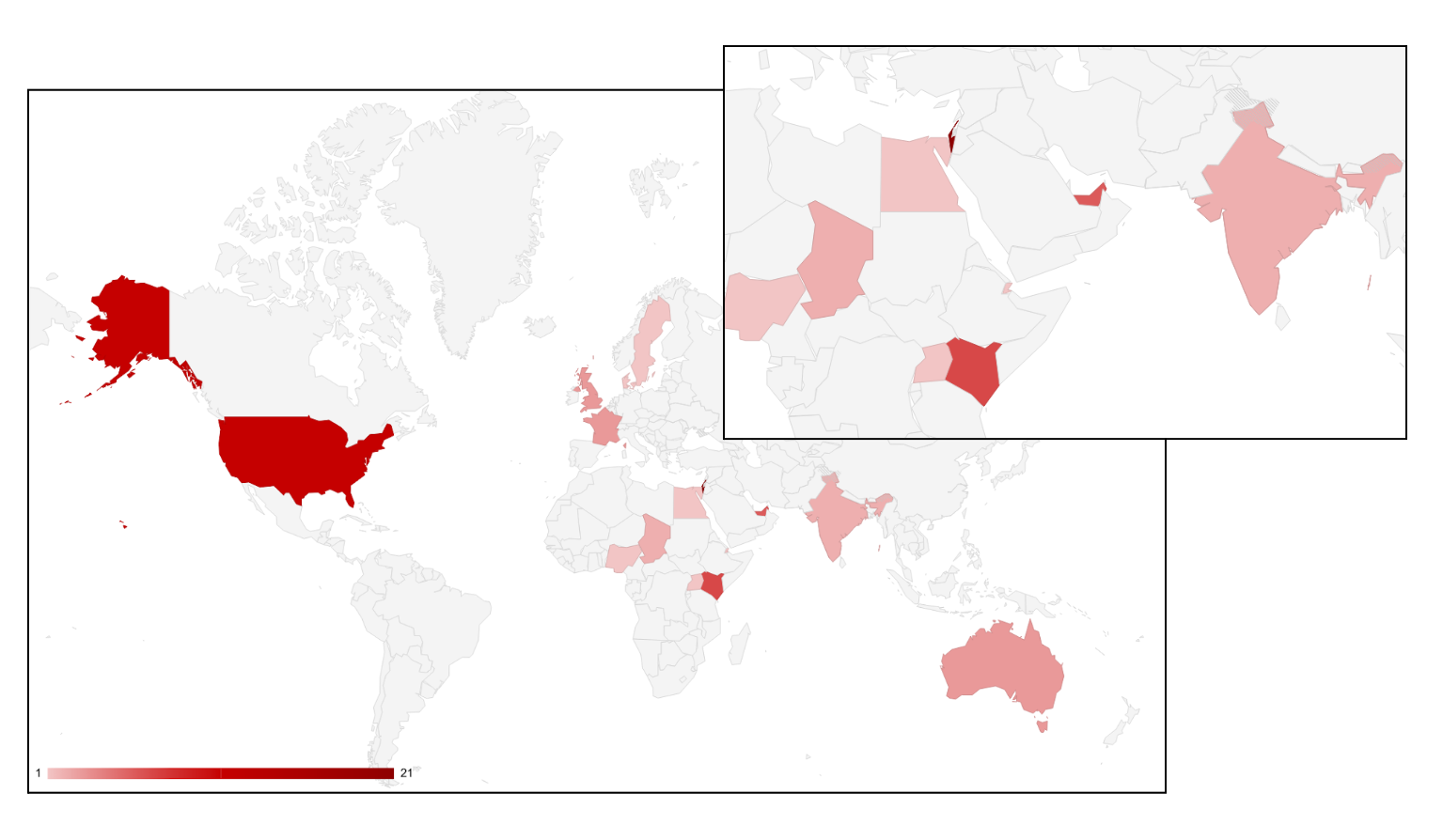
Figure 1. Map of countries frequently targeted by Anonymous Sudan
Conclusion
The unsealing of the indictment against the two Sudanese brothers behind Anonymous Sudan reveals the true nature of this hacktivist group. Their motivations, while often masked under religious or Sudanese nationalist sentiments, were primarily driven by a desire for notoriety and attention. Their sophisticated DDoS capabilities, combined with strategic social media use, allowed them to disrupt major online services and gain widespread recognition. The case of Anonymous Sudan underscores the importance of relying on factual intelligence and rigorous analysis to understand the true motivations of such groups, dispelling any previous misconceptions about their affiliations with state-sponsored actors. It also highlights the potential for significant disruption that even small, resourceful groups can cause in the digital landscape.
CrowdStrike Falcon Adversary Intelligence Premium customers can access detailed reports on Anonymous Sudan and hundreds of other adversaries through the Falcon platform, helping strengthen your defenses against attacks targeting your business. Learn more.

