Transform AWS Security Operations with Falcon Next-Gen SIEM
CrowdStrike is redefining how SOC teams turn cloud data into actionable intelligence by unifying speed, scale,…
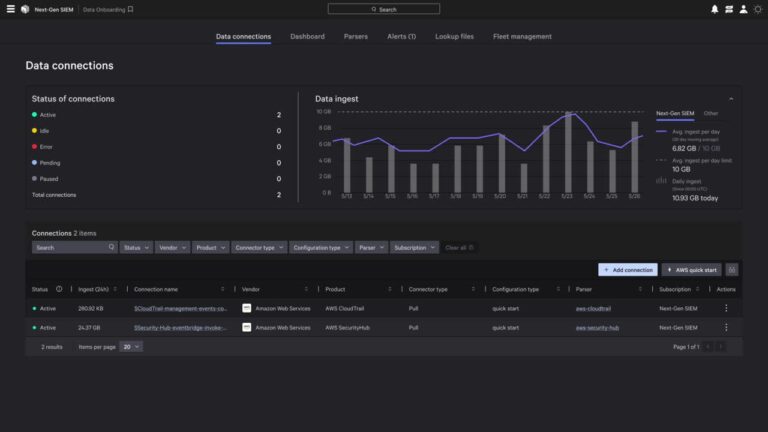
CrowdStrike is redefining how SOC teams turn cloud data into actionable intelligence by unifying speed, scale,…

Honduras is going to the the polls to elect a new president – with Donald Trump…

The Central Government has issued strict new SIM-binding rules that will change how WhatsApp, Telegram, Signal…

A tragic shooting in Washington DC has triggered sweeping policy changes in the U.S. An Afghan…

Washington DC Shooting: Trump Lashes Out After Death of National Guard Soldier #WashingtonDCShooting #NationalGuard #SarahBeckstrom #Trump…

Pete Hegseth, U.S. Defense Secretary, announced that Donald Trump has ordered 500 additional National Guard troops…

Leaders arrive for the Collective Security Treaty Organization (CSTO) summit in Bishkek. — Firstpost | News…

Have you ever encountered the “memory size exhausted” message on your website? If yes, then you’ll…

Africa’s first ever G20 summit and the first boycotted by a prominent member, has wrapped up.Its…

It’s one of the worst mass kidnappings ever seen in Nigeria. Gunmen have abducted more than…

One of the world’s premier security organizations has canceled the results of its annual leadership election…

GenAI data protection for cloud: Identify when sensitive data is transmitted from cloud workloads, services, or…

A church attack in Nigeria’s Kwara State left two people dead and several worshippers, including a…

DeepSeek-R1’s Intrinsic Kill Switch It is also notable that while Western models would almost always generate…

Have you ever opened a website and been greeted with a blank page instead of the…

Narrator: Marchand Steenkamp.About the story: Franz Walter Stahlecker was one of the architects of the Holocaust…

Anthropic’s Threat Intelligence team recently uncovered and disrupted a sophisticated nation-state operation that weaponized Claude’s agentic…

As a RunCloud user, you already know how to manage high-performance websites and servers efficiently. But…

Since 2019, the UN’s Local Communities and Indigenous Peoples Platform has expanded the Indigenous role in…

Israelis Demand Oct 7 Inquiry in Massive Tel Aviv Protest Thousands of Israelis gathered in Tel…

A deadly explosion outside Delhi’s Red Fort killed at least 12 people. Delhi witnessed its first…

AI has collapsed the vulnerability exploit lifecycle. Adversaries now discover, weaponize, and exploit exposures across hybrid…

On Thursday night-Friday morning, Russia launched a massive overnight attack on Kyiv, using hundreds of drones…

Health officials in the United Kingdom are warning that this year’s flu season for the Northern…