2025 LG 45″ UltraGear GX9 – Watch This BEFORE You Buy!
God-tier gaming monitor or minor improvement over the previous version? Let’s talk about the LG UltraGear…
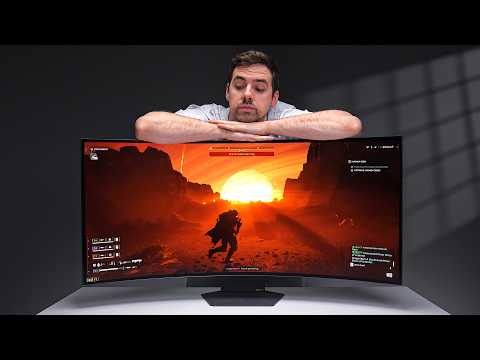
God-tier gaming monitor or minor improvement over the previous version? Let’s talk about the LG UltraGear…

The ASUS ProArt 5K PA27JCV is under half the price of the Apple Studio Display and…

Madagascar’s aye-aye: “as if fear and panic had a baby and rolled it in dog hair”…

I’ve been using the M4 MacBook Air for a few months now. Here are some things…

If you’ve been fascinated by the Erin Patterson trial, there’s another podcast you probably want to…

Launching a high-performing ecommerce site requires precision, collaboration, and attention to detail — especially for established…

South African President Cyril Ramaphosa recently used a speech as an opportunity to make a dig…

Lawyer Tania Waikato, who led an urgent Waitangi Tribunal claim before the bill was introduced, has…

cPanel has dominated the web hosting control panel market for over two decades and established itself…

Operation Sindoor LIVE: YouTuber Jyoti Malhotra, Others Arrested for “Spying” for Pakistan | Palki Sharma |…

Operation Sindoor LIVE: YouTuber Jyoti Malhotra, Others Arrested for “Spying” for Pakistan | Palki Sharma |…

If you’re counting on the 2026 midterm elections to wrest control of Congress from the GOP,…

We also need better media literacy, especially for younger audiences. Fans should be encouraged to explore…

Roughly 140 million to 100 million years ago, the piece of land that is modern day…

There is another hidden risk for those being rescued: the presence of cameras capturing professionals at…

During his years in the U.S. House of Representatives, then-Rep. David Jolly (R-Florida) was known for…

YouTube has eclipsed Netflix and Disney as the go-to streaming platform, a fact that underlines its…

It’s one of the most valuable marketing assets you can build. Email list growth and engagement…

Fines, Jail Time & Ban: Trump’s 30-Day Warning to Foreign Nationals in US | Firstpost America…

Welcome to Behind the Cart, a series where we sit down with the people behind the…

Consumers spent over $31 billion globally on subscription box services in 2023 and that market is…

The directors adopted more of a colorful 1990s aesthetic than the haunting art that originally inspired…

How much is your voice worth? It could be as little as roughly A$100. That was…

Trump Tariffs LIVE: Mexico Sends Major Drug Capos to US as Trump Tariff Threat Looms |…