How to move your custom site to WooCommerce (and why you should)
Running your ecommerce business on a custom-built platform can make scaling with flexibility and control a…
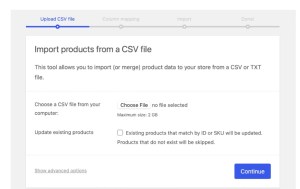
Running your ecommerce business on a custom-built platform can make scaling with flexibility and control a…

Amid a push toward AI agents, with both Anthropic and OpenAI shipping multi-agent tools this week,…

Agentic AI systems can autonomously execute actions, call external tools, and chain multiple operations together to…

CrowdStrike has been recognized as a Customers’ Choice in the 2026 Gartner Peer Insights™ Voice of…

There is a pervasive myth in the web development community: “WordPress is for novices. Real developers…

It’s worth noting that both OpenAI and Anthropic open-source their coding CLI clients on GitHub, allowing…

Types of AI Tool Poisoning Attacks Tool poisoning attacks can take many forms, each designed to…

I’m excited to announce CrowdStrike’s agreement to acquire SGNL, a leader in identity-first security. This acquisition…

Google has filed a lawsuit to protect its search results, targeting a firm called SerpApi that…

Artificial intelligence is transforming how organizations operate, innovate, and compete. From employees using GenAI tools to…

Supabase is the most popular open-source Backend-as-a-Service (BaaS) platform, which offers developers the freedom and control…

Sensitive information disclosure ranks #2 on the OWASP Top 10 for LLM Applications, and for good…

Polestar is an electric car brand with an emphasis on performance and a sustainable future. Combining…

DeepSeek-R1’s Intrinsic Kill Switch It is also notable that while Western models would almost always generate…

Zero-Day Vulnerability in Windows Kernel CVE-2025-62215 is an Important elevation of privilege vulnerability affecting Windows kernel…

Downtime costs money and credibility. For SaaS companies and online businesses, a few minutes offline can…

If your website goes down, every second counts. Uptime monitoring tools alert you before visitors or…
![How to Create a Public Status Page for Your Website [FREE]](https://massive.news/wp-content/plugins/wp-fastest-cache-premium/pro/images/blank.gif)
Your online store just went down. Support channels are flooding, and customer frustration is mounting on…

On Thursday, OpenAI and Microsoft announced they have signed a non-binding agreement to revise their partnership,…

Growing dependency on AI coding tools The speed at which news of the outage spread shows…