Today’s adversaries operate at machine speed. According to the CrowdStrike 2025 Global Threat Report, the average eCrime breakout time — from initial compromise to lateral movement — has dropped to just 48 minutes, down from 62 minutes in the previous year.
Traditional vulnerability management can’t keep up. Scheduled scans, static CVSS scoring, and manual triage create blind spots and operational lag, forcing security teams to spend hours stitching together telemetry, deduplicating findings, and debating what to fix while attackers move laterally. Most tools on the market were built to check compliance boxes, not stop adversaries.
This operational disconnect is what led CrowdStrike to rethink exposure management — not as another scanning engine or bolt-on dashboard, but as an evolving, platform-native capability.
CrowdStrike recently introduced exposure management innovations to help organizations identify and prioritize threats while managing the new attack surface introduced by generative AI. CrowdStrike’s Exposure Prioritization Agent, AI Discovery, Risk Knowledge Base, and continuous visibility are available in CrowdStrike Falcon® Exposure Management and delivered through the unified CrowdStrike Falcon® platform.
In this blog, we’ll take a closer look at the latest Falcon Exposure Management innovations and how they’re engineered to provide real-time, high-fidelity visibility and prioritization at scale.
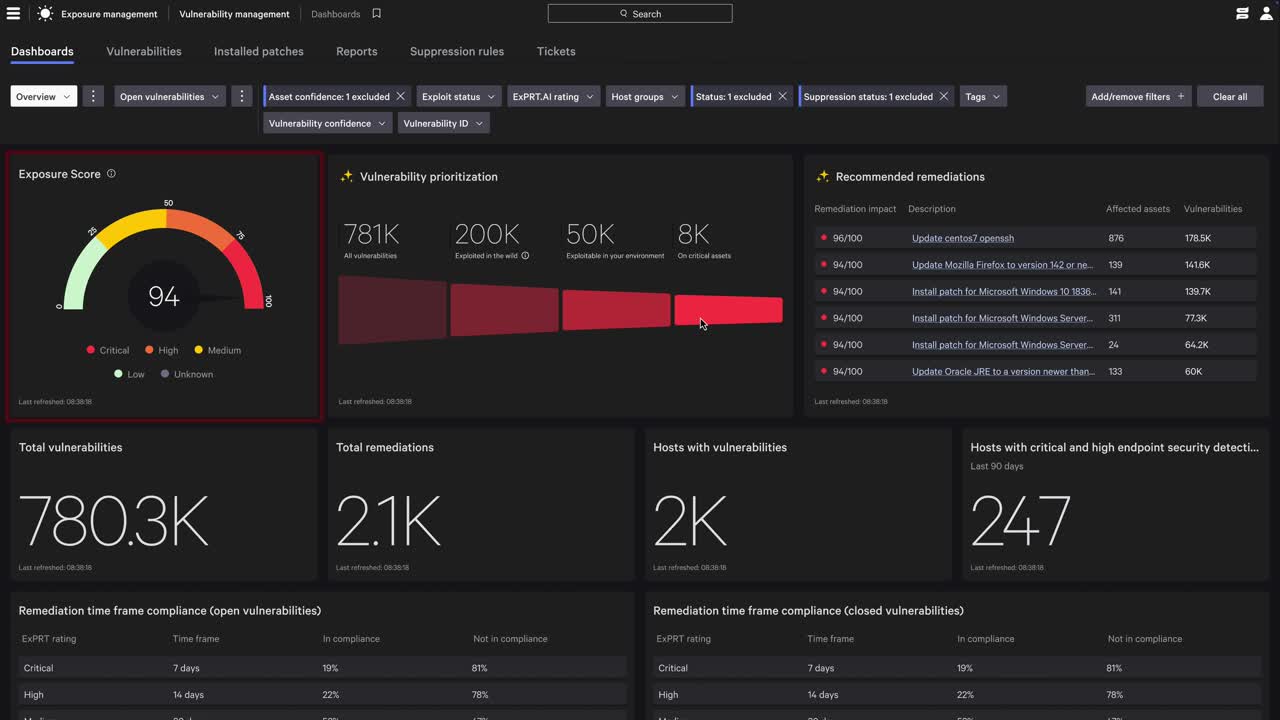
Prioritization Reimagined with Exposure Prioritization Agent
Falcon Exposure Management has long embedded ExPRT.AI to help security teams cut through CVE noise and focus on the 5% of vulnerabilities that carry the highest real-world risk. Now, we’ve taken that foundational innovation further.
The new Exposure Prioritization Agent provides context and enables real-time decision-making in exposure triage. In addition to the global dynamic risk scoring provided by ExPRT.AI, it offers local reasoning, continuously processes telemetry, exploits signals, and considers the business criticality of assets to generate high-confidence recommendations on the Falcon platform.
The Exposure Prioritization Agent is built to answer three questions in real time using live data:
-
What could an attacker do with this vulnerability?
The Exposure Prioritization Agent relies on ExPRT.AI, which enriches CVE data with exploit metadata, in-the-wild activity, and reuse of attacker tooling. It uses CrowdStrike threat intelligence and telemetry-derived insight to define what the CVE could enable — for example, privilege escalation, credential harvesting, or RCE. -
Can the vulnerability be exploited in this environment?
The agent performs environment-specific checks using host- and workload-level telemetry, including running services, kernel versions, control plane exposure, open ports, and misconfigurations. It understands whether the preconditions for exploitation exist, filtering out theoretical risk. -
What is the potential business impact?
Using the context of an asset’s purpose, criticality levels, and inter-domain relationships, the Exposure Prioritization Agent calculates downstream effects: Is the affected host domain-joined? Is it reachable via lateral movement? Does it run business-critical applications or store sensitive data?
These three lenses converge to produce a single “fix first” recommendation — a context-aware decision that is specific to the environment, prioritized by likelihood of exploitation, and aligned to business impact.
What This Means for Security Teams
The Exposure Prioritization Agent operates in-stream, using Falcon platform telemetry to evaluate exposures as they’re detected, without added overhead, tuning, or manual correlation. It integrates natively with these Falcon platform modules to accelerate triage and trigger workflows:
- CrowdStrike Falcon® Insight XDR for real-time endpoint and process telemetry
- CrowdStrike Falcon® Discover and Falcon Exposure Management’s EASM capability to correlate the internal and external attack surface
- CrowdStrike Falcon® Fusion SOAR to initiate automated remediation based on prioritized risk
- CrowdStrike Charlotte AI™ to expose the Exposure Prioritization Agent logic and allow analysts to ask why a vulnerability is prioritized
With the Exposure Prioritization Agent, prioritization becomes a reasoning engine embedded in the tech stack. Security teams no longer need to write complex correlation rules or sort through hundreds of CVEs per host to guess what matters. The agent analyzes the environment, threat activity, and CrowdStrike Enterprise Graph® in real-time to automatically deliver the correct action.
In initial deployments, customers are seeing1:
- Up to 95% reduction in remediation workload
- Accelerated triage, replacing hours of spreadsheet work
- Significant drop in false positives and low-value patching effort
Watch the demo to see how the Exposure Prioritization Agent works across real telemetry to detect exploitability conditions and automatically drive remediation workflows.
AI Discovery: Manage the AI Attack Surface
As enterprises adopt generative AI across development, IT, and data science workflows, a new layer of exposure is emerging. Copilots, LLMs, AI agents, and Model Context Protocol (MCP) servers are deployed directly into environments where they can access sensitive data, run with elevated privileges, and create novel lateral movement paths.
CrowdStrike AI Discovery, now available in Falcon Exposure Management, brings automated, contextual visibility into this AI-powered attack surface. With a single toggle in the console, security teams can now see AI components that were previously undetected. AI Discovery surfaces:
- Local or containerized LLM runtimes
- MCP servers and endpoints
- AI-specific packages from Python (pip) and JavaScript (npm) registries
- IDE plugins and browser-based copilots
- Endpoint-integrated AI agents or assistant processes
Rather than treating these assets as anomalies or unknown binaries, Falcon Exposure Management classifies them as AI-related components and ties them into the broader asset and risk context. This helps security teams immediately understand:
- Where AI code and services are running
- What systems and data do they interact with
- Whether those components are accessible from lower-privileged systems
- Whether they are shadow AI or sanctioned models
- If they introduce lateral movement or privilege escalation risk
This is especially important for AI workloads that may not trigger traditional vulnerability detection tools — for example, model-serving frameworks embedded in web apps or dev copilots that handle sensitive prompts in-browser.
How It Works
AI Discovery operates by analyzing Falcon platform telemetry in real-time. It identifies AI-relevant packages, processes, service signatures, and command-line behaviors using a combination of:
- Application fingerprinting
- Package metadata heuristics
- Command usage patterns
- Process-to-process relationships
- Marketplace integrations and context gathering
It’s fully embedded in the Falcon platform, so there’s no need to deploy a separate AI scanner or configure discovery rules. As AI components are observed, they are automatically classified and integrated into Enterprise Graph, where their risk context (e.g., internet exposure, privilege level, proximity to sensitive systems) is continuously evaluated and reported.
Why It Matters
Security teams gain a live, integrated view of how AI is adopted across their environment and where it may introduce risk. This visibility is critical for:
- Establishing AI asset inventory and baselining usage
- Detecting unapproved or shadow AI services
- Identifying potential attack vectors introduced by overprivileged or exposed AI tools
- Supporting future compliance or governance initiatives around AI safety and usage
AI Discovery reflects the value of a real-time, platform-native architecture, enabling the delivery of additional visibility at speed without requiring additional work from security teams.

