Elasticsearch is a powerful, open-source search engine and analytics platform for storing, searching, and analyzing large volumes of data in real time.
It’s critical for many modern applications and services that require fast, efficient search and analytics capabilities.
Although it is a helpful tool for analytics, Elasticsearch is not installed by default on RunCloud servers because most RunCloud users don’t need it, and having it preinstalled would simply consume resources unnecessarily if not needed.
But installing Elasticsearch on your server is easy. This article provides a step-by-step guide for installing Elasticsearch on a server managed by RunCloud.
Let’s get started!
Connect To Server via SSH
Before installing Elasticsearch, you should have a server connected to RunCloud. If you don’t have a server, you can follow our tutorial on how to set up a Vultr or AWS server on RunCloud.
Once your server is up and running, you must log in via SSH to install Elasticsearch. If you already know how to do this, jump to the RunCloud section to install Elasticsearch.
How To Add Your SSH Key To RunCloud Server
Once your server is connected to RunCloud, you can create new users and grant them access to log in to the server directly from the dashboard. First, go to the account settings and open your SSH key vault.
In the key vault, you need to add your public SSH key. You can either use your existing key or generate a new one using the following command:
ssh-keygen -t rsa
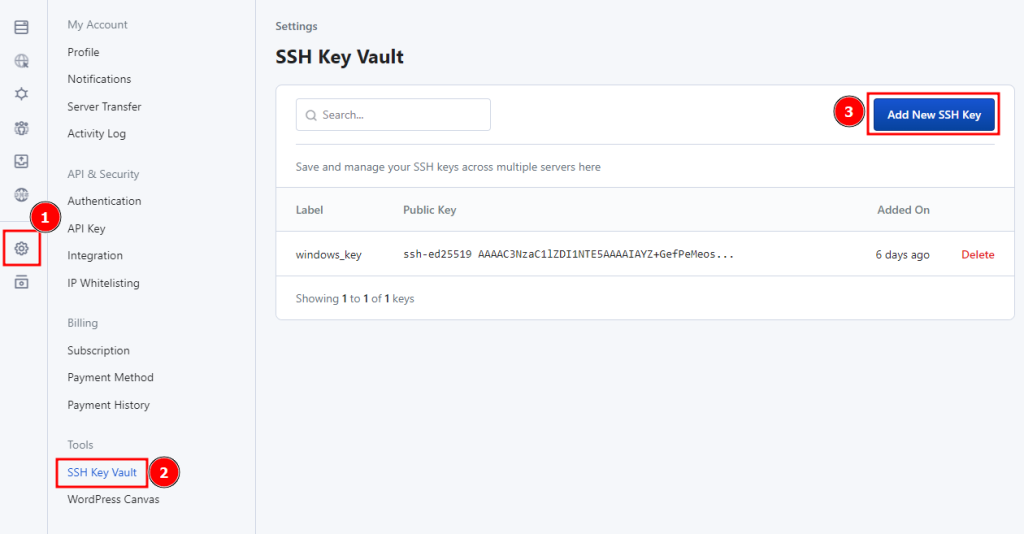
After you add the key, it will appear in the key vault. You can create a new user or add this SSH key to an existing user account on your server.
We will create a new user account to avoid disturbing files or settings in the existing user’s account. To do this, go to your server settings and open the “System User” tab. In this tab, create a new user with sudo privileges.

After creating the user, go to your server’s SSH tab and click on the “Add New SSH Key” button to use the key we just added to the vault.
On the next screen, use the saved key from the SSH key vault and select the user we just created.

After adding the SSH key, log in to your server by running the following command in your terminal. Before executing the command, add the username, IP address, and path to the private key:
ssh <username>@<ip address> -i <path to private key>Installing Elasticsearch on RunCloud
When you log in to your server, you will see a large banner saying “RunCloud.” This confirms that your login attempt was successful. All the commands executed in this terminal will run on your server.

Once you log in to the server, you can copy and paste the following commands into your terminal to import the Elasticsearch PGP Key and install it from the APT repository:
wget -qO - https://artifacts.elastic.co/GPG-KEY-elasticsearch | sudo gpg --dearmor -o /usr/share/keyrings/elasticsearch-keyring.gpg
sudo apt-get install apt-transport-https
echo "deb [signed-by=/usr/share/keyrings/elasticsearch-keyring.gpg] https://artifacts.elastic.co/packages/8.x/apt stable main" | sudo tee /etc/apt/sources.list.d/elastic-8.x.list
sudo apt-get update && sudo apt-get install elasticsearch
A lot of people use Elasticsearch with Kibana, an open source visualization tool. If you want to install Kibana on your system, you can run the following command as well:
sudo apt-get install kibana
After the installation is complete, pay close attention to the output displayed. The screen displays the default password for the Elasticsearch account. In the above example, the password is 8RF65T*6cB*Y_rjUDedn.
If you accidentally closed the screen, you can generate a new password using the following command:
sudo /usr/share/elasticsearch/bin/elasticsearch-reset-password -u elastic
Now, you can configure the Elasticsearch service to start automatically when the server reboots, and then start it using the following commands. You can optionally run the fourth command in the following block to check whether the service is up and running correctly:
sudo systemctl daemon-reload
sudo systemctl enable elasticsearch.service
sudo systemctl start elasticsearch.service
sudo systemctl status elasticsearch.service # Check statusIf you see active (running) status, then your service is configured correctly and you can start using it.

Testing Elasticsearch
After installing Elasticsearch you can test the installation by running the following command. If you receive an output similar to the screenshot attached below, then your Elasticsearch installation is working correctly.
sudo curl --cacert /etc/elasticsearch/certs/http_ca.crt -u elastic https://localhost:9200

Configuring SSL Certificates For Elasticsearch
When we tested the Elasticsearch instance, as shown in the above example, we connected using the default certificate which is generated automatically. The connection is encrypted using the http_ca.crt certificate file stored in the /etc/elasticsearch/certs/ directory.
If you’re not working in a production environment, you can turn off the TLS/SSL on the HTTP networking layer by editing the /etc/elasticsearch/elasticsearch.yml file and setting the xpack.security.http.ssl.enabled to false.
Generating Certificate Signing Requests for Elasticsearch
If you are using Elasticsearch in a production environment, there is a good chance that many people will connect to your server, so using a self-signed certificate is not a good idea in such cases.
If you are part of a large organization, you might already have a certification authority (CA) trusted by all the computers, or you might want to use a commercially available certificate authority. Having a CSR file will make issuing certificates much more manageable in both cases.
Use the following command to create a certificate signing request. The CLI tool will ask you for basic information, such as your domain name and IP address. Fill out all the necessary fields and optionally secure the certificate with a password:
sudo /usr/share/elasticsearch/bin/elasticsearch-certutil httpIf you didn’t change the default path of the output file, then your elasticsearch-ssl-http.zip file will be stored in the /usr/share/elasticsearch/ directory.
Use the following commands to unzip the file and view your certificate signing request. (Don’t forget to update the name of the .csr file to match the filename):
sudo unzip /usr/share/elasticsearch/elasticsearch-ssl-http.zip
sudo cat /usr/share/elasticsearch/elasticsearch/<mydomain>.csrThe above command will show you your certificate request document. You can use this to generate certificates – usually these are .pem or .cer files.

After you get your certificate from your CA, you can put the certificate and the keys (from the zip folder generated above) in the /etc/elasticsearch/certs/ and update the /etc/elasticsearch/elasticsearch.yml to use your new certificate.
If you configured a password during the key creation, you must add that to the key vault. You can use the following command to do so:
sudo /usr/share/elasticsearch/bin/elasticsearch-keystore add xpack.security.http.ssl.keystore.secure_passwordFor more information, refer to the Elasticsearch documentation.
Configuring Kibana
After installing and configuring Elasticsearch, we can start configuring Kibana on your server. First, we’ll ensure Kibana starts automatically after the system reboots and is running. Run the following commands to start the Kibana service and verify that it is running correctly:
# Start Kibana service
systemctl start kibana.service
# Enable Kibana to start on boot
systemctl enable kibana.service
# Verify Kibana service status
systemctl status kibana.service
In the above example, we can see that the service is up and running correctly. Once you are sure that the service is running as expected, you can start the basic configuration by navigating to the Kibana configuration directory using the following command:
cd /etc/kibanaNext, you need to edit the kibana.yml configuration file. If you need help with this, refer to our previous article, in which we explained how to edit files via SSH. Run the following command to open the nano text editor:
sudo nano /etc/kibana/kibana.ymlAfter opening the configuration file, you need to add or modify these essential configurations:
server.host: "0.0.0.0"
# Define the port Kibana listens on
server.port: 5601
server.publicBaseUrl: "https://kibana.yourdomain.com"
In this configuration, note the port number you used, as we will need it later. Once you add the configuration, you can save and close the configuration file by pressing Ctrl + X and Enter.
Next, you need to navigate to the Elasticsearch directory and generate a Kibana enrollment token:
systemctl restart kibana.service
cd /usr/share/elasticsearch
bin/elasticsearch-create-enrollment-token -s kibanaThe above command will produce a long string of text in your terminal; copy it and paste it into a notepad somewhere, as you will need it later. After that, you can execute the following commands to generate a verification code:
cd /usr/share/kibana
bin/kibana-verification-codeThe above command will generate a 6-digit code. Write it down, as you will need it in the next step.
Configure a Proxy service
After configuring the above settings, you can access your Kibana server by navigating to your server’s IP address on the specified port. However, if you want it to be accessible via a simple domain name, you can configure a Nginx reverse proxy from the RunCloud dashboard.
We have already written a documentation post about setting up a Proxy from the RunCloud dashboard. When following this guide, edit the pre-populated fields to enter the port number you saved earlier. Once you save the Nginx config, you can access your Kibana dashboard via a URL. After configuring this, you can also consider setting up an SSL certificate for your dashboard.
Accessing Kibana Dashboard
Navigate to your web application’s specific URL. If you follow this guide correctly, you will be greeted with a Kibana welcome screen.
On this screen, you will be asked to enter the authentication token and the six-digit verification code you saved earlier. Once you enter them, Kibana will take a minute or so to initialize everything.

After your installation is complete, you will be asked to enter the login credentials for the dashboard. You must enter the credentials created during the “Installing Elasticsearch” step. For example, in this tutorial, the username is “elastic” and the password (which was automatically generated) is “8RF65T*6cB*Y_rjUDedn”.

After entering the login credentials, you should be able to access your Kibana dashboard.
After Action Report
Elasticsearch is an essential tool for anyone who needs to store, search, and analyze large volumes of data. By following the article’s step-by-step guide, you can quickly and easily set up Elasticsearch on your RunCloud-managed server and take advantage of its powerful capabilities.
If you’re tired of managing your own servers – check out RunCloud’s fast, efficient, and visual cloud server management service. RunCloud is built for developers who want to focus on shipping great work, not managing their infrastructure.
With RunCloud’s user-friendly interface and powerful features, managing your server has never been easier. It offers a painless server configuration, so you don’t need to spend hours figuring it out.
Get started with RunCloud today and get up and running in minutes.
