Most approaches to CDR don’t address the speed of today’s threats. While adversaries move with greater speed and stealth, defenders are constrained by:
-
Lagging detection and response: Reliance on slow cloud log processing creates unacceptable windows of exposure.
-
Too many signals, not enough insight: The volume and volatility of cloud telemetry make it difficult to distinguish genuine threats from background noise and allow adversaries to slip through unnoticed.
-
Limited response automation: Traditional cloud workload protection (CWP) tools can block or isolate compromised instances but can’t take action across the cloud control plane, leaving defenders to perform containment manually.
The latest adversary trends demand a new approach to cloud detection and response that is real time and harnesses the power of agentic AI.
Introducing Real-Time Cloud Detection and Response
CrowdStrike is introducing new CDR capabilities to help SOC teams respond to these challenges and outpace modern adversaries. The result is a battle-tested, real-time approach to cloud defense centered around three key innovations.
Real time detection engine processes cloud logs in seconds
Falcon Cloud Security has implemented a new approach which processes cloud logs as they stream in and instantly applies detections to reduce the detection latency from minutes to seconds.1
This approach was invented and developed by the CrowdStrike Falcon® Adversary OverWatch™ threat hunting team, which has battle-tested and refined it over the past decade to improve accuracy, scale, and performance.
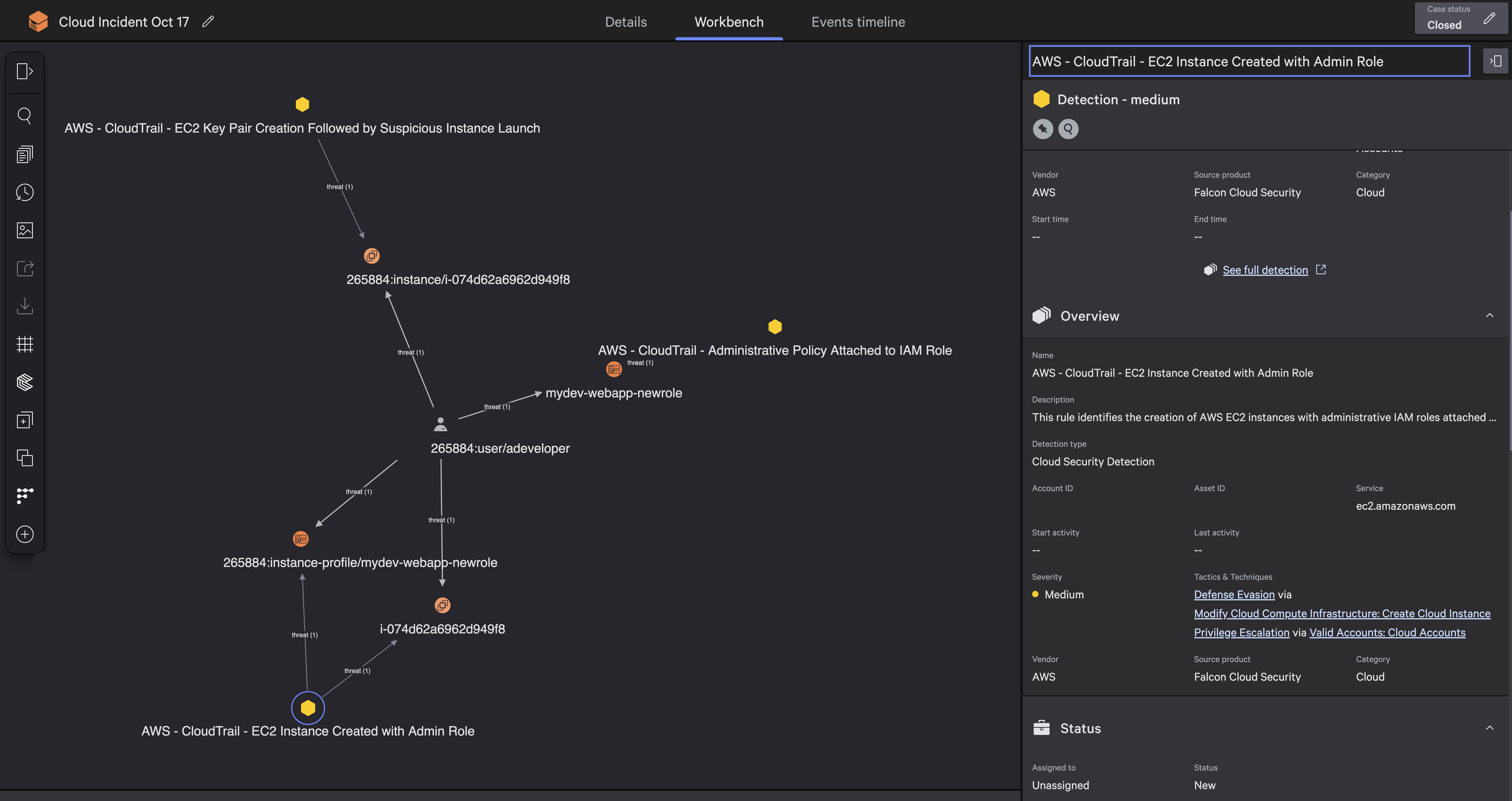
By eliminating detection lag and reducing mean time to detect (MTTD) from minutes to seconds, Falcon Cloud Security removes a critical bottleneck in reducing overall MTTR and helps ensure cloud threats are detected and triaged the moment they occur.
New Real-Time Cloud Indicators of Attack Identify Cloud Threats
CrowdStrike Falcon Cloud Security has expanded its library of out-of-the-box (OOTB) detections to identify advanced cloud-specific adversary behaviors that map to the MITRE ATT&CK® framework in real time. These detections apply deep cloud context, such as asset inventory data, to identify sophisticated threats such as privilege escalation attempts and malicious CloudShell activity the moment they occur. CrowdStrike cloud indicators of attack (IOAs) are seamlessly integrated in a unified view alongside endpoint and identity detections, enabling cross-domain case creation and threat investigations.

